Picture a world where every keystroke is a potential landmine, and every click could trigger a cascade of consequences.In the darkened underbelly of the digital realm, where shadows dance across lines of code and encryption serves as both fortress and weapon, emerges a cyber saga that sends shivers down the spine of cybersecurity experts worldwide.Let’s delve into the tale of Lockbit Ransomware group – a nefarious force that transcends mere lines of binary to orchestrate a symphony of chaos in the interconnected web of our modern age.
Imagine this: a single click, a malicious email, and your entire network is held hostage. Files encrypted, operations crippled, data threatened to be splashed across the dark web for the world to see.This is the nightmare LockBit specializes in, its potency a chilling cocktail of innovation and ruthlessness.LockBit doesn’t just encrypt data; it wields the double-edged sword of “double extortion.” While your files are locked away, your secrets are siphoned off, a ticking time bomb ready to detonate your reputation if the ransom isn’t met.
Join me on a rollercoaster ride through the labyrinthine corridors of the dark web, where anonymity is power and every byte tells a tale of cybernetic vendetta.
BEFORE WE BEGIN
-
Ransomware: Ransomware is a malicious software designed to block access to a computer system or files until a sum of money, often in cryptocurrency, is paid to the attacker. This form of cyber threat encrypts the victim’s data, rendering it inaccessible, and typically displays a ransom message demanding payment in exchange for the decryption key. Ransomware attacks have become a pervasive and sophisticated threat, targeting individuals, businesses, and organizations worldwide, with the potential for severe financial and operational consequences.
-
Dark Web: The dark web is a hidden part of the internet that is intentionally concealed and requires specific software, such as Tor, to access. Unlike the surface web, which is indexed and searchable by conventional search engines, the dark web operates on encrypted networks, fostering anonymity and privacy. While the dark web serves legitimate purposes, it is notorious for hosting illicit activities, including the sale of stolen data, illegal drugs, hacking tools, and various cybercriminal services. It is a complex and clandestine digital environment where users often remain anonymous, contributing to the challenges faced by law enforcement in combating cybercrime.
LOCKBIT
This cybercrime syndicate, first bubbling to the surface in 2019, has become a hydra-headed monster, its tentacles slithering into the networks of corporations and governments alike.The group is backed by hundreds of affiliates who take care of the ‘breakin in’ phase, aka, infiltration into vulnerable networks. Its weapon? A potent cocktail of ransomware, extortion, and psychological warfare.LockBit isn’t just another malware blip on the radar. It’s a juggernaut responsible for an estimated 44% of all ransomware attacks globally in 2022, according to a joint statement by several government agencies. That translates to thousands of crippled businesses, millions in stolen data, and a trail of digital destruction in its wake.
Originating in the murky realms of the dark web, this shadowy collective has meticulously honed its expertise in deploying highly sophisticated ransomware attacks, encrypting the digital lifelines of corporations and organizations with ruthless precision.
LOCKBIT INFECTION PHASES
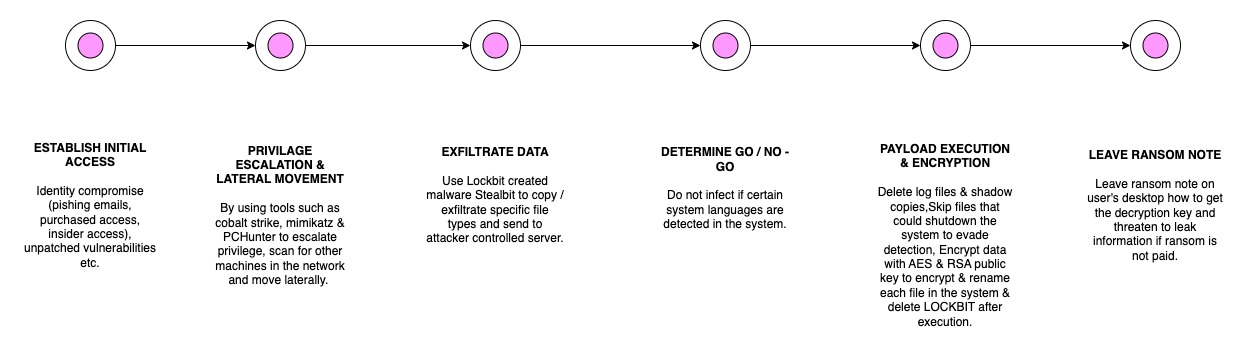
ANATOMY
Lockbit Ransomware has the following anatomy
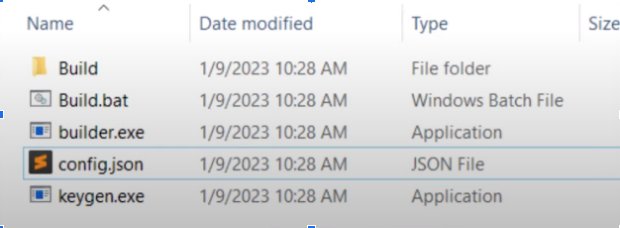
Build.bat Used to generate the build files in the build folder including LB3.exe, LB3_Pass.exe,Password_exe.txt & LB3Decrypter.exe
Builder.exe
Config.json Used to adjust various configuration parameters
Keygen.exe
The LB3.exe is responsible to encrypt the files on the machine and it will change the icon of the files & generate a text file on the desktop with instruction.
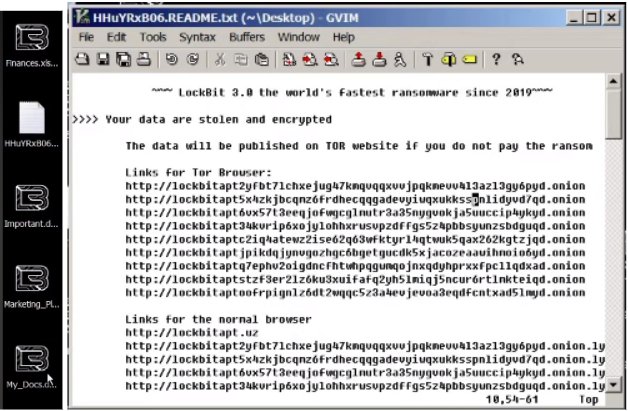
RANSOM NOTE
Once the encryption is done lockbit encrypts all the files on the system, changes the file extension to .lockbit and leaves a ransom note.
DOUBLE EXTORTION
Gone are the days of simple file encryption. LockBit elevates ransomware to a whole new level with its double extortion strategy. This brutal two-pronged attack involves:
-
Data Exfiltration: Before encryption, LockBit steals your sensitive data, including financial records, customer information, and confidential documents. This stolen data becomes the bargaining chip, with the threat of its public release hanging over victims’ like a Damocles sword.
-
Data Encryption: LockBit utilizes powerful algorithms to scramble your files, rendering them inaccessible and unusable. This creates immediate disruption and panic, pressing victims to pay the ransom quickly.
This double-pronged approach amplifies the pressure on victims, significantly increasing the likelihood of them paying the ransom.
TRIPLE EXTORTION
In August 2022, LockBit announced that it would use triple extortion on its victims adding DDoS attacks on top od Double Extraction techniques.
RaaS (Ransomware as a Service)
LockBit operates as a “Ransomware-as-a-Service” (RaaS) model renting out its malicious tools to anyone with an internet connection and malicious intent. These malicious actors, like digital mercenaries, target vulnerable systems, encrypt files and demand exorbitant ransoms in exchange for the decryption key.This democratization of cybercrime has several alarming implications:
-
Lower Barrier to Entry: Aspiring cybercriminals no longer need advanced technical skills to launch ransomware attacks. They can simply purchase access to LockBit’s tools and infrastructure, lowering the overall barrier to entry for cybercrime.
-
Wider Attack Surface: The RaaS model allows LockBit to cast a wider net, targeting a more diverse range of victims, from small businesses to large corporations.
-
Increased Attack Volume: With a larger pool of attackers, the number of LockBit-related attacks is bound to increase, further saturating the cybercrime landscape.
OTHER TRAITS
- Attacks Windows and Linux: Initially, they had targeted only Windows systems, but LockBit 2.0 was improvised to attack Linux systems as well.
- Bug Bounty: LockBit conducts bug bounty programs to improve their defenses and establish that they are professional hackers. Anyone who finds a flaw in their malware kit is rewarded generously.
- Marketing: They actively market towards affiliates to join them and carry out attacks.
- ZCash: LockBit 3.0 introduced ZCash payment options for collecting ransom from victims, as well as for paying their affiliates, with less disruption from law enforcement.
- Exfiltrator-22: A new attack framework was created by affiliates of the former LockBit 3.0 operation that includes features found commonly in other post-exploitation toolkits, but has added features that enhance ransomware deployment and data theft. The EX-22, as it is referred to, is designed to spread ransomware quickly in corporate networks while evading detection.
- AV and EDR: The LockBit ransomware group started a campaign in early January 2023, that used combinations of techniques effective against AV and EDR solutions.
- Exfiltrate Data: In a recent campaign, the LockBit gang introduced a new method to allow it to exfiltrate data from high-profile organizations by bypassing the Mark of The Web (MOTW) protection mechanism.
- Avoids Certain Languages: LockBit 3.0 also checks the victim’s UI language before carrying out an attack. They avoid infecting systems with the following languages: | Language | Country | |————————|———————-| | Arabic (Syria) | | | Armenian (Armenia) | | | Azerbaijani (Cyrillic Azerbaijan) | Azerbaijan | | Azerbaijani (Latin Azerbaijan) | Azerbaijan | | Belarusian (Belarus) | Belarus | | Georgian (Georgia) | Georgia | | Kazakh (Kazakhstan) | Kazakhstan | | Kyrgyz (Kyrgyzstan) | Kyrgyzstan | | Romanian (Moldova) | Moldova | | Russian (Moldova) | Moldova | | Russian (Russia) | Russia | | Tajik (Cyrillic Tajikistan) | Tajikistan | | Turkmen (Turkmenistan) | Turkmenistan | | Tatar (Russia) | Russia | | Ukrainian (Ukraine) | Ukraine | | Uzbek (Cyrillic Uzbekistan) | Uzbekistan | | Uzbek (Latin Uzbekistan) | Uzbekistan |
ATTACK VECTORS
LockBit doesn’t rely on just one trick to breach your defenses. Here’s a closer look at some of its most common attack vectors, along with resources to stay informed and protected:
1. Phishing Emails:
LockBit crafts convincing emails disguised as legitimate sources like banks, delivery services, or even government agencies. They use urgent language, official logos, and spoofed email addresses to trick users into clicking malicious links or opening infected attachments. These links can download malware or lead to fake login pages that steal your credentials.
2. Software Vulnerabilities:
LockBit actively scans for unpatched vulnerabilities in popular softwares and web browsers.These weaknesses often align with Common Weakness Enumerations (CWEs) a standardized catalog of software and hardware vulnerabilities.They exploit these known weaknesses to infiltrate systems without needing user interaction.This highlights the importance of keeping software up-to-date with the latest security patches.
3. Weaponizing Stolen Credentials
LockBit purchases stolen credentials from the dark web, bypassing the need for exploit or brute-force attacks.These credentials, often leaked through data breaches or phishing scams, provide the group with instant access to victim systems, bypassing traditional security measures.
4. Exploiting Zero-Day Vulnerabilities:
LockBit doesn’t just rely on readily known vulnerabilities. It possesses a hidden weapon exploiting zero-day vulnerabilities, software flaws so new that no patch exists. This gives LockBit an alarming advantage, allowing it to infiltrate systems before anyone knows they’re exposed.
5. Recruiting Insiders for Corporate Network Breaches:
LockBit actively recruits disgruntled or financially motivated insiders within corporations to act as accomplices.These insiders provide valuable access by sharing credentials, planting malware, or disabling security measures, giving LockBit a clear path to infiltrate the network and deploy its ransomware.
6. Abusing Legitimate Tools:
LockBit doesn’t always rely on flashy malware.The group cleverly exploits built-in Windows tools like PowerShell and PsExec to navigate undetected within compromised networks. These tools, originally designed for legitimate system administration, become weapons in LockBit’s hands, allowing them to escalate privileges, move laterally, and ultimately deploy their ransomware payload.
VICTIMS & RANSOMS
Since its inception, LockBit has ensnared over 2,000 victims, racking up a staggering $91 million in ransom demands just in the US alone ![1]. In 2022, it was responsible for a mind-boggling 44% of all ransomware attacks globally (source: CISA).
And 2023 was no different. LockBit maintained its dominance, claiming an even higher 52% of global ransomware attacks in the first half of the year alone (source: Trend Micro). This translates to an estimated 3,000+ victims globally, pushing the total number likely past 5,000 + since its emergence.
MAJOR EXPLOITS
2024
-
Windows Defender SmartScreen Zero-Day Vulnerability (CVE-2024-21412): This vulnerability is classified as a Security Feature Bypass. It enables attackers to bypass Windows Defender SmartScreen’s security warnings with specially crafted files, allowing them to covertly infiltrate their victims and carry out further malicious acts.
-
ConnectWise ScreenConnect Vulnerability (CVE-2024-1709 & CVE-2024-1708):
-
CVE-2024-1709 – Authentication Bypass Vulnerability.ConnectWise identified CVE-2024-1709 as a critical authentication bypass vulnerability with the highest possible CVSS severity score of 10. By requesting the “/SetupWizard.aspx/” endpoint with virtually any trailing path value, threat actors can gain access to the setup wizard on already-configured ScreenConnect instances, overwrite existing user data, and execute code remotely by creating ScreenConnect plugins.
-
CVE-2024-1708 – Path Traversal Vulnerability: CVE-2024-1708 is a high-severity path traversal vulnerability affecting the same ScreenConnect versions as CVE-2024-1709. Once CVE-2024-1709 is exploited to take control of a device, CVE-2024-1708 can be leveraged to achieve remote code execution (RCE) on the instance.
-
2023
-
Windows Print Spooler (CVE-2023-22222): LockBit targeted this vulnerability to gain remote code execution on unpatched Windows systems, potentially leading to ransomware deployment.
-
Apache HTTP Server mod_proxy_ajp (CVE-2023-0494): This vulnerability allowed LockBit to execute code on servers running Apache HTTP Server, enabling potential ransomware deployment.
-
Citrix NetScaler Bleed (CVE-2023-4966): This vulnerability allowed LockBit to bypass password requirements and multi-factor authentication on Citrix NetScaler appliances, potentially leading to ransomware attacks.
2022
-
Apache Tomcat Ghostcat/Catalina/Manager Applications (CVE-2022-22950): This vulnerability facilitated remote code execution in Tomcat servers, allowing LockBit to compromise web applications and deploy ransomware.
-
Citrix ADC and Gateway Appliances (CVE-2022-27547): LockBit exploited this vulnerability to bypass authentication and gain remote access to Citrix systems, potentially impacting critical infrastructure.
-
FortiOS Secure Sockets Layer (SSL) VPN (CVE-2022-0778): This vulnerability allowed LockBit to decrypt VPN traffic and potentially steal sensitive data or deploy ransomware on connected devices.
2021
-
Log4j2 (CVE-2021-44228): This critical vulnerability in the popular logging library allowed LockBit to execute remote code and gain initial access to victim systems. (CWE-78: Improper Neutralization of Input During Web Page Generation (Cross-site Scripting))
-
Microsoft Exchange Server ProxyShell (CVE-2021-34473, CVE-2021-34523, CVE-2021-31207): These chained vulnerabilities enabled LockBit to bypass authentication and gain unauthorized access to email servers. (CWE-79: Improper Neutralization of Input in Web Service Requests).
Few Notable Attacks:
2024
January:
- Saint Anthony Hospital - a hospital network in Chicago
- Subway - a US based restaurant chain
February:
- Motilal Oswal - a financial services organization in India
- Contra Costa Health Services - a Californian health and human services provider
- Clackamas Community College - a community college in Oregon
- La Colline Skincare - a cosmetic company based in Switzerland
March:
- Government Pensions Administration Agency in South Africa
2023
- January: Australian government’s Department of Defense attacked by LockBit
- February: American Dental Association suffers patient data breach from LockBit
- March: Marriott International hotel chain experiences guest reservation disruptions due to LockBit attack
- April: Nvidia Corporation experiences data theft due to LockBit attack
2022
- January: LockBit disrupts financial services at the Bank of Zambia.
- February: University of Pisa’s research data compromised by LockBit.
- March: City of London faces municipal service disruptions from LockBit.
- April: Scottish Environment Protection Agency grapples with environmental monitoring disruption caused by LockBit.
- May: UK’s National Health Service experiences healthcare disruptions due to LockBit attack.
- June: LockBit impacts electronics manufacturing at Foxconn factory in Mexico.
- July: Bank of Indonesia hit by LockBit, disrupting financial services.
2021
- June: LockBit 2.0 arrives with faster encryption and enhanced features.
- July: Global consulting firm Accenture falls prey to LockBit.
- August: Bangkok Airways suffers flight disruptions due to LockBit attack.
- October: French Ministry of Justice becomes a LockBit target.
2020
- January: LockBit enters the RaaS (Ransomware-as-a-Service) scene.
- September: LockBit unveils its website for attack announcements and victim leaks.
PROTECTING YOURSELF FROM RANSOMWARE ATTACKS:
Keep Software Updated: Regularly update your operating system, applications, and firmware on all devices. These updates often include security patches that fix vulnerabilities exploited by ransomware.
Back Up Your Data: Create regular backups of your important files and store them securely offline, such as on an external hard drive or in the cloud. This way, you can restore your data even if it’s encrypted by ransomware.
Be Wary of Emails and Attachments: Don’t click on suspicious links or open unknown attachments in emails, even if they appear to be from someone you know. Phishing emails are a common way for ransomware to spread.
Enable Strong Passwords and Multi-Factor Authentication (MFA): Use strong, unique passwords for all your online accounts following PCIDSS guidelines and enable MFA whenever possible. This adds an extra layer of security to prevent unauthorized access.
Reassess and simplify user account permissions: Limit permissions to more strict levels to limit potential threats from passing undeterred. Pay special attention to those accessed by endpoint users and IT accounts with admin-level permissions.
Clean out outdated and unused user accounts: Some older systems may have accounts from past employees that were never deactivated and closed. Completing a check-up on your systems should include removing these potential weak points.
Be Cautious on Public Wi-Fi: Avoid accessing sensitive information or downloading files on public Wi-Fi networks as they are less secure.
Have a comprehensive enterprise cyber security solution in place: While LockBit can try to disable protections once in a unit, enterprise cyber security protection software would help you catch file downloads across the entire organization with real-time protection.
WHAT PROTOCOLS SHOULD YOU FOLLOW IF YOU EXPERIENCE A BREACH IN INDIA
Disconnect the Affected Devices: Immediately disconnect your device from the internet or local network to prevent further infection and the spread of ransomware within your organization’s network.
Report the Attack: File a complaint with the Indian Cyber Crime Coordination Centre (ICCC) through their website (https://i4c.mha.gov.in/) or by calling their 24/7 helpline at 1930.
Seek Professional Help: Consider contacting a data recovery specialist or IT security professional to assess the situation and explore possible data recovery options. They can also advise on additional security measures to strengthen your defenses.
Do Not Pay the Ransom: Paying the ransom doesn’t guarantee you’ll get your data back and encourages future attacks. Law enforcement recommends against paying.
OPERATION CRONOS THE END ?
The recent takedown of LockBit sent shockwaves through the cybersecurity world. Operation Cronos was an international coalition of 10 countries led by British crime agency and FBI has arrested the members of Lockbit group.Two Russians were charged on the grounds of deploying Lockbit ransomware against companies around the world.
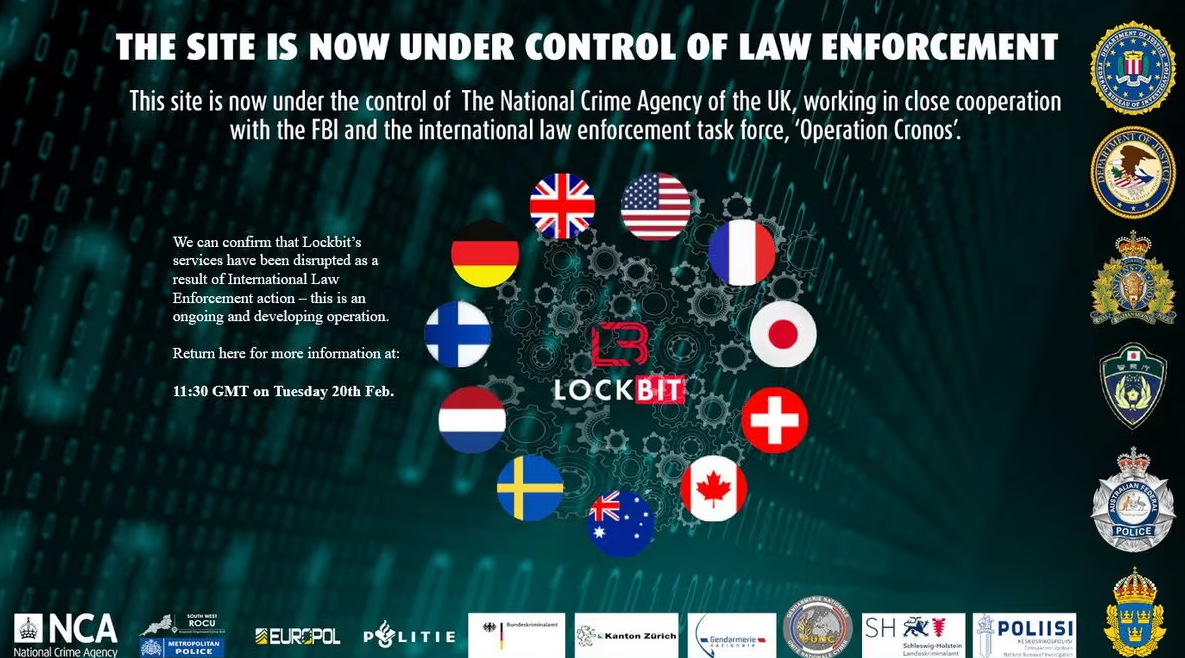
The NCA, U.S. Department of Justice, FBI and Europol gathered in London and announced the disruption of Lockbit Ransomware group which had targetted more than 2000 victims and extorted $120 million in ransom payments and Lockbit Ransomware group’s websites on the dark web were seized.
Operation Cronos seized Lockbit’s infrastructure (including their leak site), 34 servers, closure of 14,000 rogue accounts, and the freezing of 200 cryptocurrency accounts, and 5 indictments against members of the group.
Graeme Biggar, director general of the National Crime Agency had told the journalists WE HAVE HACKED THE HACKERS and taken control of their infrastructure.
While LockBit’s disruption is a positive step, the battle against ransomware is far from over.The LockBit takedown offers a window of opportunity. We must learn from their tactics, strengthen our defenses, and foster international cooperation to stay ahead of the curve. By remaining vigilant and proactive, we can build a more secure digital future where cybercrime has less room to flourish.
CITATIONS
https://thehackernews.com/2023/11/lockbit-ransomware-exploiting-critical.html
https://www.trendmicro.com/vinfo/us/security/news/ransomware-spotlight/ransomware-spotlight-lockbit
https://www.securin.io/articles/all-about-lockbit-ransomware
https://www.youtube.com/watch?v=6PEA0nFyc0Q
https://socradar.io/windows-smartscreen-vulnerability-exploited-darkgate/
https://censys.com/connectwise-screenconnect-cve-2024-1709-cve-2024-1708/
https://arcticwolf.com/resources/blog/operation-cronos-the-takedown-of-lockbit-ransomware-group/
https://www.weforum.org/agenda/2024/02/lockbit-ransomware-operation-cronos-cybercrime/
Image Courtesy : Generated using AI (Adobe Firefly)